Tech Investment Blueprint: Cyber Maturity DIY Roadmap with Optional vCISO Guidance
October 22, 2025

At Virtual Graffiti, we go beyond providing technology, we act as your guide where you need us and happy to see you grow and build stronger cybersecurity defences. We are here when you need us, guide you on your cybersecurity journey, helping you cut through vendor noise, make the right investment decisions, and implement the right controls at the right time. Whether you’re building your security foundation or advancing to the next stage, we provide the strategic oversight and practical expertise to protect your organisation and reducing your costs.
How can I protect my organisation and improve cybersecurity using the 4 Stages of a Maturity Model?
All organisations have very thinly spread resources, and cybersecurity often becomes just one of many competing priorities. The situation in Small and medium-sized organisations is even more challenging when a single person or a small team of people looks after all IT initiatives.
We tend to operate with just enough knowledge and skills to keep things running. Meanwhile, we’re constantly reminded that " your cybersecurity is only as strong as your weakest link. " It’s tempting to go all-in with a single vendor, turning on every feature they offer in hopes of increasing security. But without the right foundation in place, this approach often adds complexity without meaningful benefit. It' s like building one side of a house, complete with walls and a roof, while neglecting the foundation for the rest.
We often rely on an array of partners, suppliers, and vendors. All are willing to help. However, without a clear plan, investments often become uneven, leaving gaps in coverage or duplicated effort. The reality is that most businesses can’t afford a dedicated cybersecurity expert, let alone a part-time CISO.
This brief guide aims to provide sufficient information to IT managers and Business owners to assess their current state of IT and cybersecurity maturity. Help to prioritise, align technology investments, and improve security in a structured, achievable way.
First, let’s remember the right approach from People > Process > Technology in this order. Without people, nothing else would make sense. Technology delivers the best ROI when People also have appropriate Processes. For example, a Backup solution may not deliver expected results if there are no People or the right Processes to monitor and test the recovery procedure on a regular basis.
Many organisations rely on Essential 8 (AU) or Cyber Essentials (UK), the 18 CIS Critical Security Controls, or other compliance frameworks. They help many organisations to gain access to good practices.
For the vast majority of organisations, we would recommend keeping things simple. When you develop cybersecurity defences over a period, you are likely to gain sufficient knowledge and expertise to make better decisions. It is also likely that by the time you reach the Advanced Stages of your cybersecurity maturity, you will be able to make your own decisions, follow a more comprehensive framework, and possibly even hire an expert to provide you with guidance. Hence, we will not spend much time at this moment to describe the 4 level of cybersecurity maturity as you will likely to be able to build it yourself by that time.
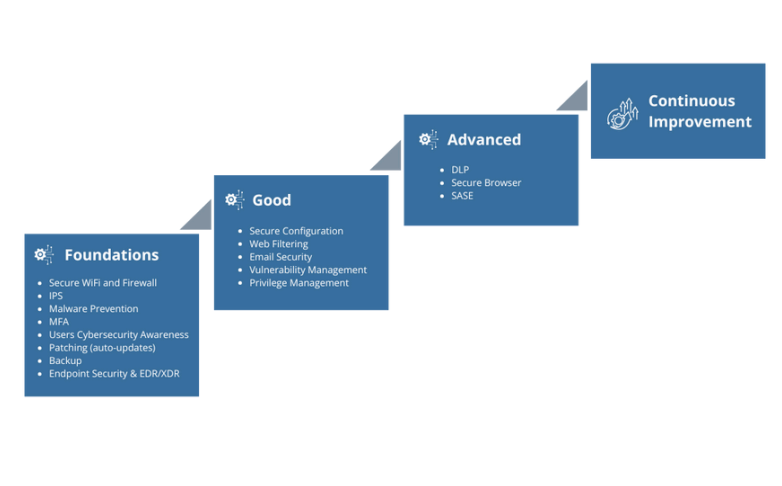
The Four Stages of Cybersecurity Maturity
1 Foundation: focus on getting basic things in place. Try not to stretch your resources and implement everything according to just one vendor recommendation. Enable basic things first, schedule a review in 3 months or so, and see if you are ready to make the next step on your journey. For example, investing in Vulnerability Management solutions would makes more sense if you already have processes to install software updates. These can be as simple as enabling such functions that are part of virtually all products from vendors. These can be more comprehensive if you use a 3 party Software Patching solution. However, in most cases, Small and medium-sized organizations can rely on what is provided out of the box by vendors without spending more on advanced Patching solution
1.1 Keep a list of all software licenses and devices you purchased. It will help you with the support renewals and avoid situations of purchasing more devices and licenses than needed.
1.2 Install a modern aka Next Generation Firewall from vendors like Fortinet, PaloAlto Networks, Sophos, or if you already have experience with SonicWall or WatchGuard you may prefer to use products from them
1.3 Enable Intrusion and Malware Prevention functions on those firewalls. These are easy to implement in comparison to more advanced features like DLP.
1.4 To boost your cybersecurity defences tenfold, implement 2 Authenticator tokens. Consider using Microsoft or Google Authenticators. If you prefer a physical fob that generate a secure code, have a look at RSA, Deepnet or those that can be inserted into a USB port to unlock a computer from Yubico. This tech protects your users even if they use a weak password.
1.5 Enable auto updates on all your products. Microsoft, Google, Apple and all others have them enabled by default. Only disable them if you have a strong reason for it
1.6 Make sure that all your users store data in places where you can back them up. In most cases you are likely using Microsoft OneDrive or Google Drive. These are highly resilient solutions. However, you can further benefit from a dedicated backup solution. Ransomware attackers often get control of OneDrive and GDrive and demand ransom. If you have a separate backup solution, you can always rely on it should you need it. Consider Veeam and Acronis. One need to start with the most important data items for the organisation. It can be customer purchases, drawings, recipes. Start with a backup for them.
2.1 If your organisation requires additional controls on your systems. Consider using dedicated solutions that can not only report any configuration changes but also protect from unauthorised changes. These are extremely important for Critical Infrastructure solutions and support your compliance efforts.
2.2 To protect your users from accessing potentially harmful websites, you can usually configure Web filtering and DNS security features on your firewalls and/or endpoint protection applications
2.3 Most organisations use Microsoft or Google email services. You should maximise value from their standard email security features. Additionally, you can sign up for more advanced email protection services from Anomali, Check Point, and Proofpoint, to name a couple.
2.4 If you feel overwhelmed with your software patching efforts. It will be beneficial to have a look at solutions that can detect and prioritise patching installations. For organizations under 200 users, we recommend free solutions such as ActionOne. For organizations that are larger we recommend solutions such as Tenable.
2.5 One of the most critical aspects of cybersecurity is the need to protect passwords. Especially administrator type passwords that exist on every device you have on your network. While password managers are now provided by Google and Apple to improve your cybersecurity practices consider a Privilege Access Management solution. These go beyond password safekeeping and provide more granular controls, regular auto password updates, and powerful features, especially for those organisations that work with multiple 3 party organisations who have access to company system
3.1 When you have good processes and cybersecurity practices in place and ready to make further steps to boost your defences. First, hire a cybersecurity company that can check and confirm that you implemented vendors ' solutions according to their recommendations and industry best practices. You can do such checks earlier and more regularly, but they are much more critical at this stage than before. You can even consider a full security audit and to obtain certification like ISO 27001.
3.2 When you are at more Advanced stages of your cybersecurity program, you can consider more specific products and solutions for your industry. For example, a Data Loss Prevention solution can be desirable even at earlier stages in financial organisations and organisations with strong R&D departments.
3.3 Many organisations can consider Endpoint Detection and Response and other variations from many vendors. At the beginning of your cybersecurity journey, you can probably benefit most by using what is available from Microsoft Windows Defender. However, at the Advanced level, it' s time to consider alternatives and gain advanced protection levels. If you find those solutions too complex to manage, you will be surprised to find service offerings from Managed Security companies or even vendors of such solutions directly. They can even work with your other 3 party systems
3.4 Secure Browsers are gaining popularity as they simplify protection from a lot of internet-born threats. Such solutions require additional efforts to manage and can be more beneficial to larger organisations. However, the trend is moving to meet simplicity and other requirements often associated with smaller organisations.
4.0 At stage 4 of your cybersecurity program, you likely have good people, processes, and tools in place. Yes, you probably feel a need for more investments, better training for your staff, and improvements to your processes. Here, you are likely to be in a real need to have a dedicated person to look after your cybersecurity, as you simply don’t have much time to drive it yourself. However, whichever route you take forward, don’t hand over your program to someone else and forget. At the end it’s you who spearheaded this and will likely have better knowledge on why certain decisions were made at the time. This knowledge is priceless, even if documentation is great
Recommended Vendors by Stage
- Firewalls: WatchGuard, SonicWall, Sophos, Fortinet, Palo Alto
- WiFi: Ruckus, Ubiquiti, Meraki
- MFA: Microsoft, Google, Yubico
- Backup & DR: Veeam, Acronis, Commvault
- Email Security: Microsoft, Google, Proofpoint
- Vulnerability Management: Rapid7, Tenable
- Endpoint Security: Sophos, ESET, Microsoft Defender
Final Thoughts
Many of the vendors mentioned above offer products and solutions that can support you across the Foundational, Good, and Advanced stages. While some advanced features may come at an additional cost, many capabilities can be unlocked through proper configuration rather than extra spending. However, the most critical factor in realising these benefits is having the right processes and people in place.
If you need further advice, help to procure any mentioned or other IT products. You can reach out to Virtual Graffiti crew.
4 Stages of a Maturity Model – Recommended Vendors
| Category | Foundations | Good | Advanced | Continuous Improvement |
|---|---|---|---|---|
| Firewalls (NGFW & UTM) | WatchGuard, SonicWall, Sophos | Fortinet, Palo Alto | At this stage you can probably make your own recommendations. | |
| WiFi | Ruckus, Ubiquiti, Fortinet, Meraki | |||
| MFA Tokens | Microsoft / Google Authenticators, Yubico, Deepnet | RSA | ||
| Cybersecurity Awareness | Barracuda, KnowBe4 | |||
| Patching | Standard Auto Updates, Action1 | N-Able, Qualys, Tanium | ||
| Backup & DR | Veeam, Acronis | N-Able, Commvault | ||
| Secure Configuration | AirLock Digital, Tanium | |||
| Email Security | Microsoft, Google | Anomali, Proofpoint, Avanan | ||
| Vulnerability Management | Rapid7, Tenable | |||
| Privilege Access Management | CyberArk, Keeper | |||
| Endpoint Security & EDR/xDR | Sophos, ESET | Microsoft Defender, Fortinet | ||
| Secure Browser | Palo Alto, Island | |||
Foundations: focuses on basic protections and essential tooling that provide the best value for your money.
Good: more integrated, capable solutions, often suitable for scaling environments
Advanced: often tailored solutions that require deeper expertise and are often associated with Enterprise
Continuous Improvement: requires internal expertise, policies, and well-defined procedures.
Many of the vendors mentioned above offer products and solutions that can support you across the Foundational, Good, and Advanced stages. While some advanced features may come at an additional cost, many capabilities can be unlocked through proper configuration rather than extra spending. However, the most critical factor in realising these benefits is having the right processes and people in place.
If you need further advice or help procuring any mentioned or other IT products, you can reach out to the Virtual Graffiti crew.
