
As society confronts a major pandemic, Novel Coronavirus (COVID-19) is impacting nearly all people around the world. Schools are closed, travel is restricted, events cancelled, and offices emptied – all with the goal of stemming the spread of COVID-19. The Center for Disease Control has even suggested employers establish polices that allow their employees to work remotely to promote social distancing. Heeding the call, businesses have rapidly mobilized to meet the threat, and as a result, more people today are working from their homes than at any time in modern history. And just to give you an idea of how disruptive that may be, according to a study, the remote workforce in America grew 159% between 2005-2017. It’s safe to say that today, due to the coronavirus outbreak, we are looking at vastly higher numbers.
While the response to coronavirus has been unprecedented, for many businesses this “work-from-home” experiment launches them into decidedly unfamiliar territory. In this blog post, WatchGuard outlined the strategies for maintaining business continuity during the coronavirus outbreak.
We face risks in cybersecurity every day. However, one of the challenges of enabling a mobile workforce is that the chances of being the subject of cyber attacks can increase significantly. Without the benefit of your core network protections, a user on the go could become infected without your knowledge, and even introduce the infection to your broader environment when they reconnect with your network.
Hackers exploit coronavirus fears
It seems hackers will take advantage of any major news story or world event to launch their attacks. At a time of heightened fear, your employees’ email and social media accounts are flooded with news reports, comments, videos, and links about the virus. Unfortunately, cyber criminals are exploiting fears to phish your users, hack their systems, or deliver malware.
Here are just a few examples of how threat actors are taking advantage of coronavirus:
Off-Network Newbies
COVID-19 is driving aggressive work-from-home policies, with businesses shuttering offices and sending the bulk of their employees to work from home full time almost overnight. While workplace flexibility is now the norm for many businesses, the average company sees around only 30% of their workforce working from home at a given time. Many companies have struggled to provide the resources needed to keep folks secure when working from home, issuing hastily provisioned laptops, or sending them home with desktops never intended to be taken off the secure network. Not only do these devices need security now that they are off network, its important that we make sure they don’t introduce malware and other threats when they re connect to the network, either by VPN or returning to the office.
VPNs Are Overloaded
With coronavirus scattering employees to their homes, VPN usage has skyrocketed, with researchers noting a 50% increase in traffic in a one-week period. The United States alone is expected to increase VPN use by 150% in a month’s time. The sudden migration of users from corporate to home offices has left many businesses scrambling to provide VPN licenses to their employees. The risk is that without VPN connectivity, users will not have access to the resources they need or they will use insecure connections to access them.
Bandwidth Bedlam
It’s not just your employees who are home. With schools closed, many of your coworkers will have children at home continuing their education remotely, gaming, or simply surfing the web. Both parties will quickly gobble up bandwidth, especially when using resource-intense applications like video conferencing. Places hardest hit by the virus have seen over a 90% increase in Internet use. In response, many ISPs are upgrading their customers to faster, higher bandwidth offerings, or eliminating data caps to avoid overages.

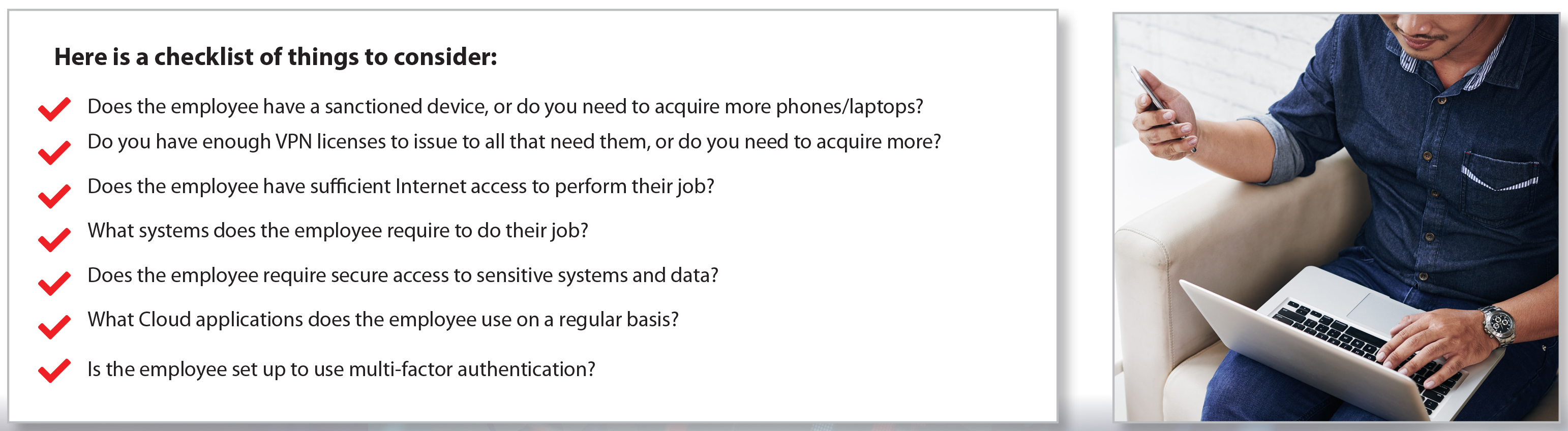
1. INVENTORY AND ASSESS YOUR COMPANY’S REMOTE WORK CAPABILITIES
While 92% of businesses offer remote work, the opportunity has not been afforded to all employees equally. For many companies, this shift to remote working happened almost overnight, leaving little time for adequate planning. Now is the time to audit and assess the new network access your company needs and consider the security implications. Managed Security Services Providers (MSSPs) are experts in security assessment, and can help midsize businesses quickly come up to speed and get their users what they need.
For network nomads, who are always on the go, chances are they have the resources they need for the long haul. For the folks who haven’t worked from home as much, it is helpful to take an inventory of all of the data and applications they may access regularly. From there, you can map out what needs to be accessed, who needs access, and how best to provide that access. Work with department heads to understand the unique needs of their team and make sure their team members are set up for success.
2. SET AND COMMUNICATE EXPECTATIONS FOR REMOTE WORK
As many of your employees are likely working from home for the first time, now is a great time to reach out to your team to outline your company’s work-from-home policy to set expectations for employees working remotely. Some 24% of businesses haven’t updated their work-from-home policy in over a year, so use this as an opportunity to do so. A simple email, or conference call with your team, can go a long way.

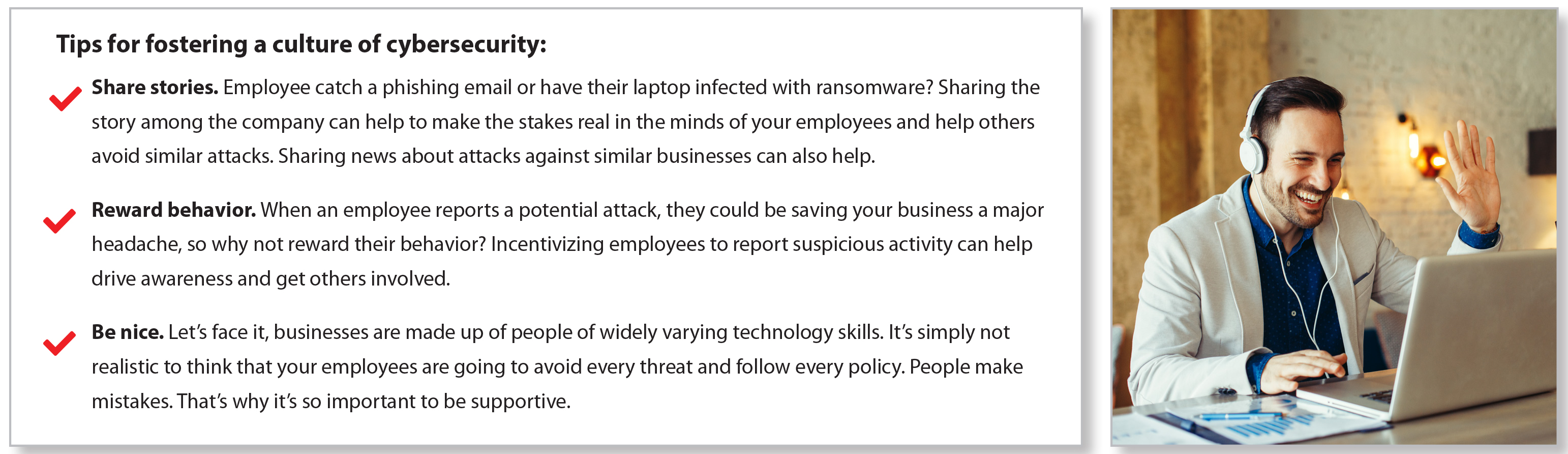
3. FOSTER A CULTURE OF CYBERSECURITY
Most business leaders understand that the culture of a workplace is an important part of what drives its success or failure. They must also come to understand that the same dynamics exist in cybersecurity. As your employees are under threat from targeted attacks, in some instances impersonating members of your team, corporate culture often ends up being the difference between intercepting the attack or infecting your entire network.
Hackers use techniques to manipulate and influence your users into taking the action they want, using authority and urgency as a weapon. As a leader, you should encourage open channels of communication, so when an employee, even at the lowest levels of the organization, sees something they believe is a threat they feel empowered that their concern will be taken seriously.
4. IMPLEMENT MULTI-FACTOR AUTHENTICATION
As companies grapple with having the predominance of their workforce working remotely, securing access to internal tools presents a major challenge. At the same time, hackers are increasingly targeting credentials, placing your users’ account information directly in their crosshairs. For this reason, we recommend deploying multi-factor authentication (MFA) to all of you users, so they are fully authenticated every time they connect to your network.
Multi-factor authentication also allows you secure access to Cloud applications and environments that remote workers might access directly from the Internet, adding an additional layer of protection at a time when businesses are most vulnerable.

5. EXTEND VPN ACCESS TO PRIORITY USERS
Secure connectivity to corporate headquarters and critical applications is essential if your employees are going to maintain productivity as they work remotely. Virtual Private Networks (VPNs) add a layer of security to private and public networks, allowing individuals and organizations to send and receive data safely over the Internet.
Generally, your users will require one of two VPN types:

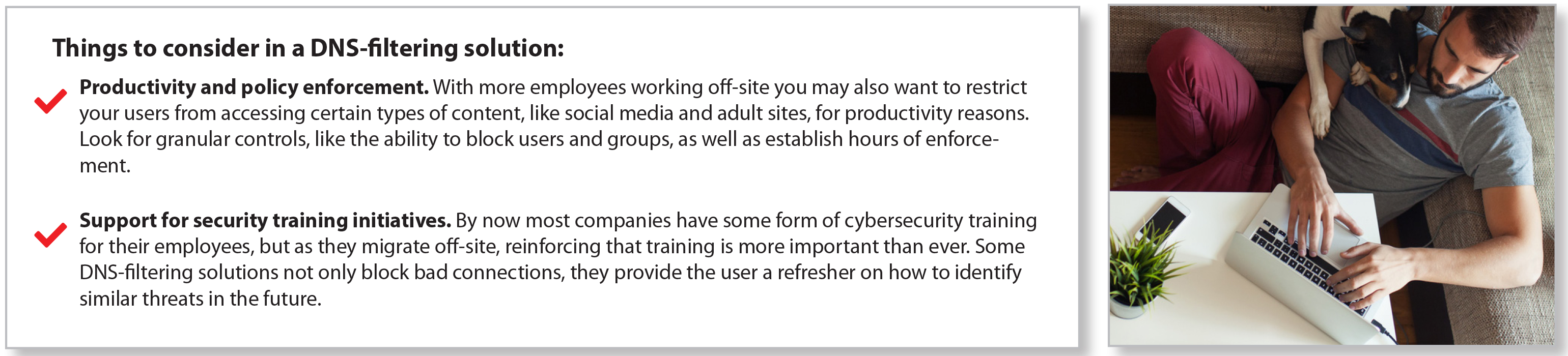
6. KEEP USERS SAFE FROM RISKY CLICKS WITH DNS FILTERING
Keeping users safe as they navigate the Internet is more difficult when they are connecting from outside of your network. With employees stuck at home, chances are good that company laptops will be used for a hefty amount of personal web surfing and email checking. Cloud-based DNS filtering makes it possible to block connections and limit access to the risky areas of the Internet. Clicks on malicious links or attempts to connect to domains related to phishing and malware can be prevented, without having to use a VPN.
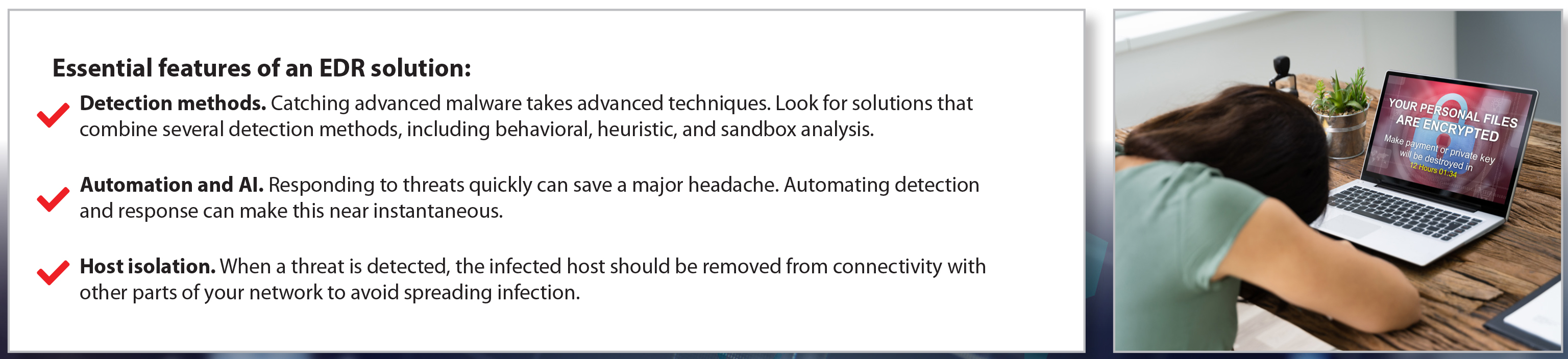
7. KEEP ENDPOINTS FREE OF MALWARE
Malware and ransomware threats have only accelerated as a result of coronavirus. And the risk of infection has never been higher, as users may no longer benefit from the protection of a firewall when working from home. While endpoint antivirus solutions will catch many of the threats, they are powerless against evasive, zero day malware that we see all too often. Endpoint detection and response (EDR) solutions can not only detect these advanced threats, they can kill the threat and return the infected device to good order, 100% remotely.
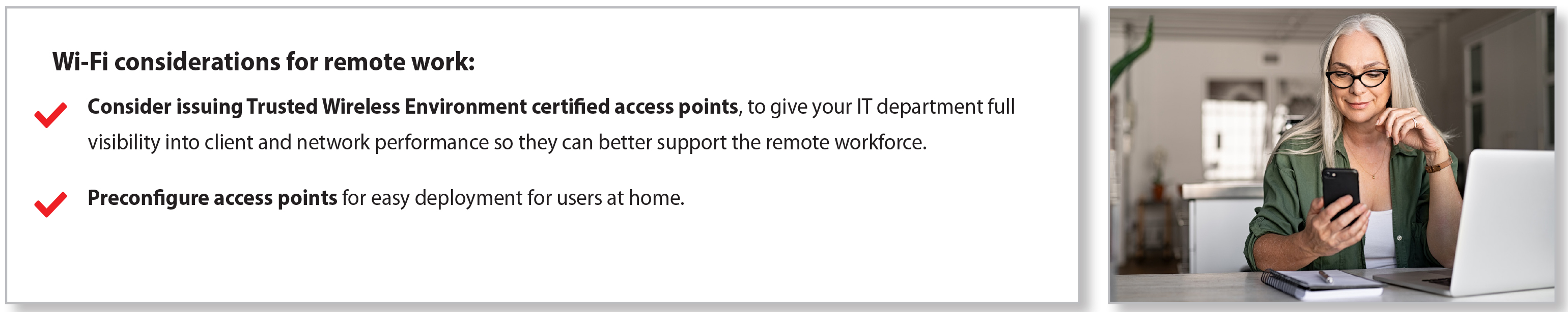
8. Retain Control of Wi-Fi
Working from home can introduce security concerns related to Wi-Fi as well. For remote workers located in dense housing areas such as apartments or condos, every Wi-Fi device including doorbells, gaming consoles, and IoT devices can be a way in for malicious neighbors looking to eavesdrop. Nefarious neighbors could exploit the fact that their building is full of folks working from home, with Wi-Fi making up nearly 50% of all IP traffic.

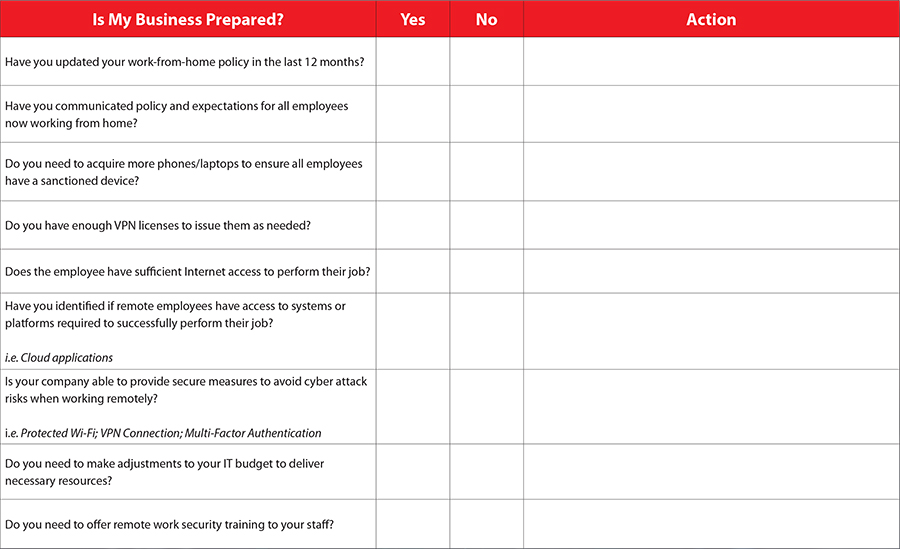
Simply put, there are things you can’t predict. Business leaders know there will be bumps on the road and unplanned events along the way. So, what can you do to protect your business future? A preparedness plan does not promise perfection, but it can give you the tools to securely navigate challenges and provide necessary resources to ensure operational continuity.
Today it is the coronavirus outbreak, but it could be anything and more than just disasters. A major event like The World Cup that disrupts how a city normally functions, or even human error can push your business to go on critical preparedness mode. Any situation that forces you to adapt quickly to unexpected changes is the ultimate proof of how important it is to truly understand your organization and what needs.
Why? Because it shows your employees, customers, and stakeholders that your company can thrive even during unprecedented events. Yes, it’s great for your brand, but more importantly, it creates great sense of trustworthiness in your community. Plus, you’ll have an incredibly valuable story for years to come.

We are here to help small and midmarket companies during the current unprecedented events.
Don't miss out on our sales events and all our big promotions, subscribe to our email and enjoy exclusive weekly deals from Virtual Graffiti!