

Protect against compromised identities and credentials

Protect against compromised identities and credentials

Protect against compromised identities and credentials

Protect against compromised identities and credentials
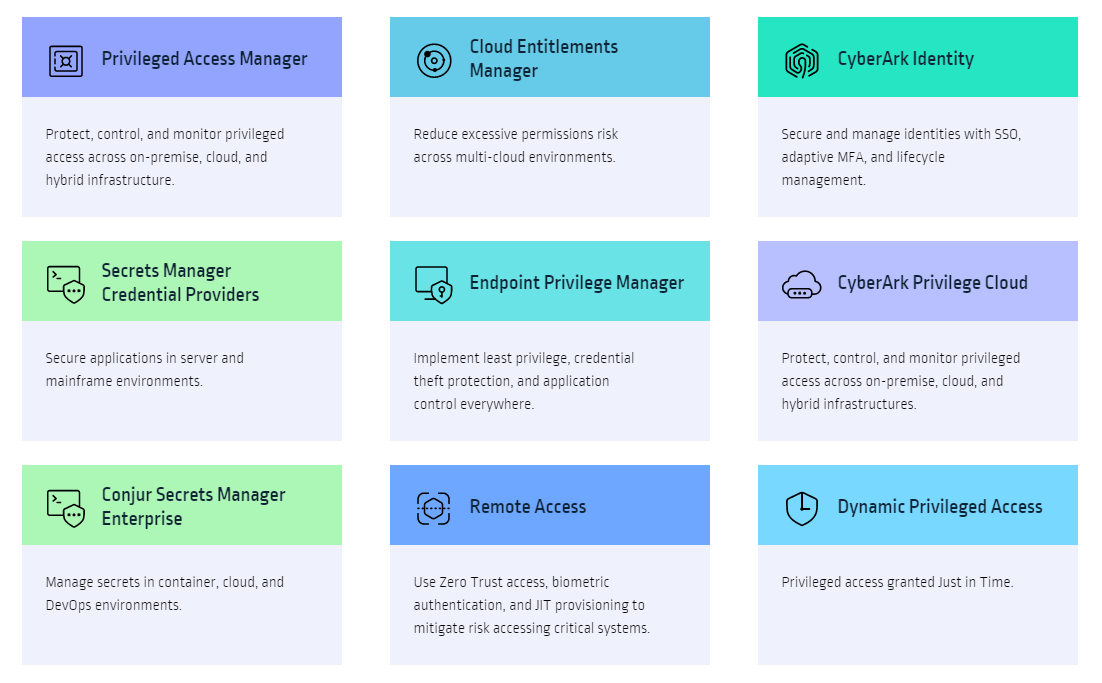
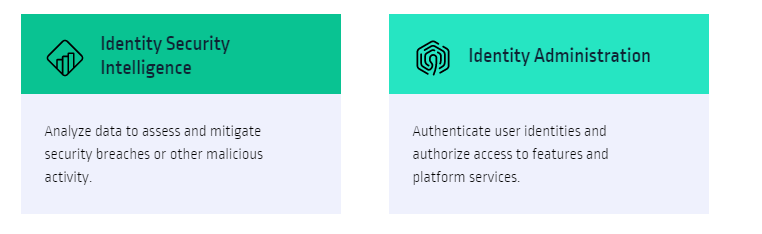
Apply least privilege security controls. Protect privileged access across all identities, infrastructure and apps, from the endpoint to the cloud.

Protect against the leading cause of breaches — compromised identities and credentials.

Deliver digital experiences that balance security and a frictionless experience.

A unified solution to address identity-oriented audit and compliance requirements.

Consolidate key security technologies and simplify policy enforcement.

Improve business agility to deliver great digital experience.

A privilege-centric approach to securing identities.

Give your distributed workforce the tools they need – without compromising security.
Application code within the digital supply chain are an increasing target for sophisticated cyber attacks. With CyberArk, you can help ensure security across the DevOps pipeline while driving business agility and a frictionless experience for developers.

Keep application and automation tools secure without slowing down developer velocity.

Give applications easy access to the credentials they need, while keeping secrets out of reach for attackers.

Reduce complexity and burden on developers while improving agility and protection of the business.